security management
Information security practices have evolved from Internet perimeter protection to an in-depth defense model in which multiple countermeasures are layered throughout the infrastructure to address vulnerabilities and attacks. Layering is necessary because of increased attack frequency, diverse attack sophistication, and the rapid nature of attack velocity.
Network access points and systems are probed thousands of times each day in an attempt to exploit vulnerabilities. Modern blended/hybrid attacks use multiple and deceptive attack methodologies to gain unauthorized system access and control from outside and within organizations. The proliferation of worms, day-zero attacks, viruses, Trojan horses, spyware, and attack tools challenges even the most fortified infrastructures, resulting in shorter reaction time and costly remediation.
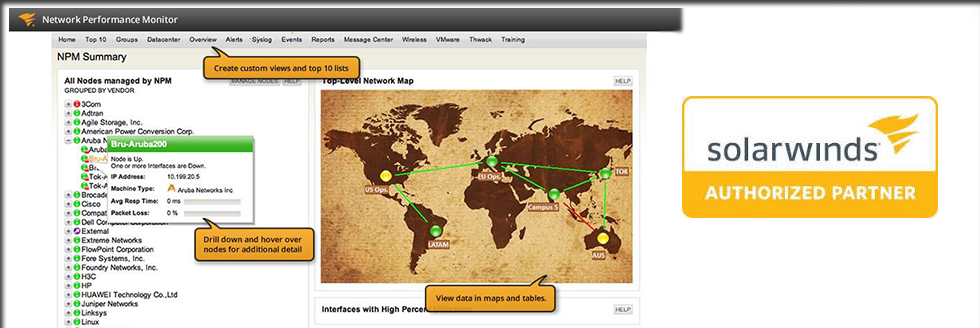
In addition to the number of servers and network devices, each security component offers isolated event log and alert features for anomaly detection, threat reaction, and forensics. Unfortunately, this isolation yields a tremendous amount of noise, alarms, log files, and false positives for operators to discern or effectively utilize. In addition, compliance legislature requires strict data privacy, improved operational security, and documented audit processes.
 |
|